What is the Secure Web Proxy on Google Cloud?
Secure, control and monitor your egress traffic in your Google Cloud environment.
In my study for Cloud Security Engineer certification I'm discovering little-known, obscure services - i.e. ones that don’t get much fanfare but are definitely worth knowing about. Last week, I wrote about Cloud EKM and today we’re talking about the Secure Web Proxy (SWP).
Originally available in preview as of October 22 back in 2022, and then going GA in May 22 the year after (so it’s 8 months old as of today), as the name suggests the SWP is a service that acts as a middleman for your traffic egressing out of your VPC to the web. From the documentation:
Secure Web Proxy is a cloud first service that helps you secure egress web traffic (HTTP/S). You configure your clients to explicitly use Secure Web Proxy as a gateway.
But it’s very hidden away and not advertised anywhere really. In fact I only came across it by accident when I was reviewing some serverless architectures in the architecture center (which is AWESOME by the way, check it out if you haven’t already).
This is what I was reviewing: https://cloud.google.com/architecture/serverless-functions-blueprint. I noticed one of the tools hiding in plain sight in the “shared VPC host project” called the “Secure Web Proxy” and thought to myself: “That’s strange, I haven’t heard of that before”.
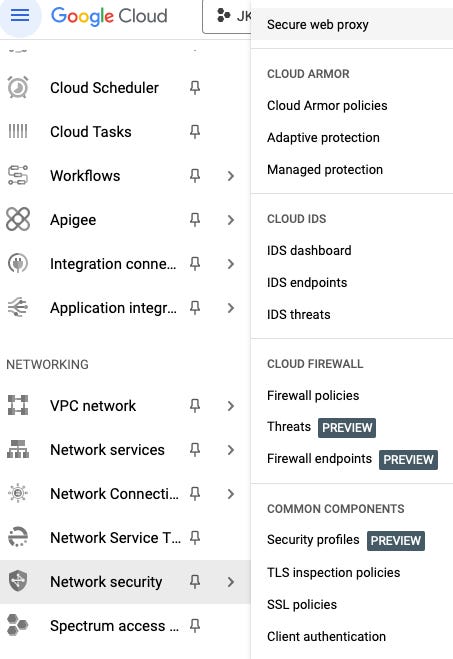
In fact it’s so hidden that even the menu option to find it doesn’t have it’s own heading section. Take a look at the screenshot. You have to scroll all the way down to network security and then in the pop out menu, it’s hiding all the way up the top.
Once you’ve found it and clicked through enabling several APIs you can create the SWP. Some things to keep in mind:
It only supports VM’s, containers, serverless envs that use the connector (so no direct VPC access yet!) and workloads that are in another cloud or on prem connected to your VPC via Cloud Interconnect or VPN.
You need to configure your clients to use the proxy. Traffic is not sent through it by default.
Only IPv4 is supported.
You need to use a NAT gateway that is enabled only for the SWP endpoint in that region.
If those caveats don’t scare you off, then perhaps it’s worth setting up for your environment. The SWP helps you control which external web services your egressing traffic can connect to.
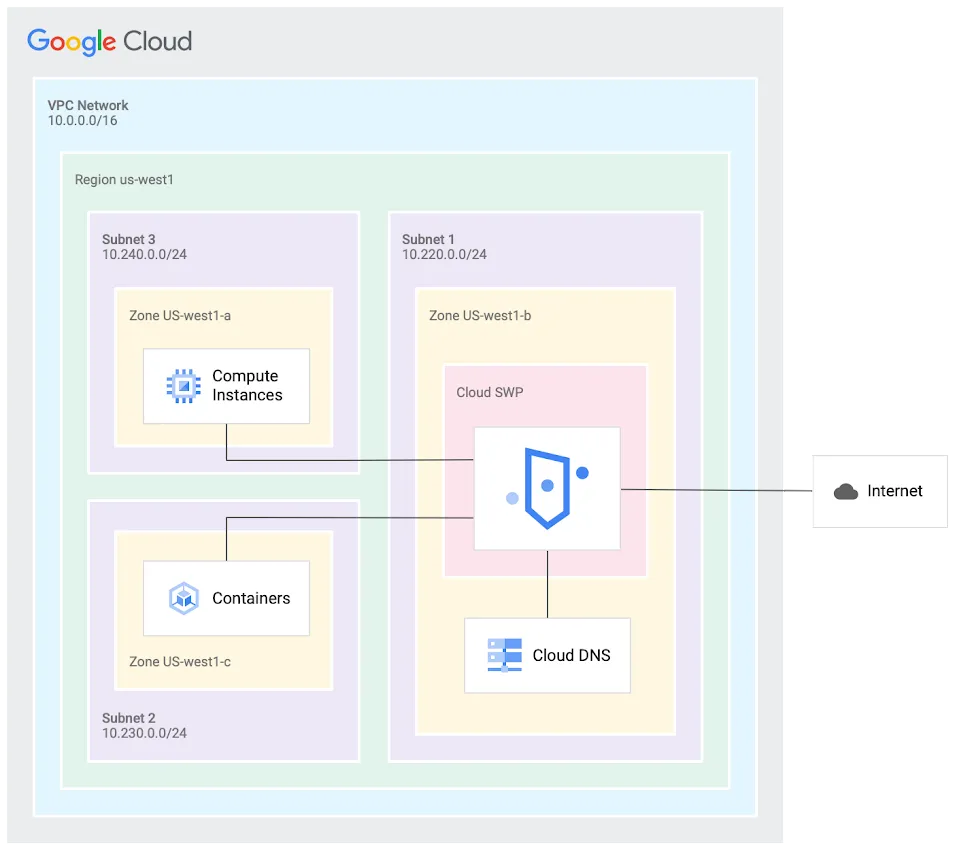
Here’s a sample architecture diagram showing how the SWP could fit into a network topology:
In the docs for the SWP, it talks to a number of benefits/features
SWP config is a deny all by default
Modular egress access policies
Source identity based on tags, service accounts, ip addresses
Autoscaling
No VMs to configure or setup and doesn’t require updates to maintain security. After you’ve configured the policies it works out of the box.
End to end encryption for the proxy tunnels.
SWP supports HTTP/S CONNECT for client-initiated end to end TLS connections.
Integration with Cloud Audit logging and operations suite.
At the risk of regurgitating all of the docs here, I’ll stop there, but there’s a whole lot that the service offers.
The last thing worth mentioning is the pricing for this service. It’s pretty straightforward pricing, which is good, because it doesn’t exist in the pricing calculator!
0.018 USD per gigabyte of data processed.
1.25 USD per hour the gateway is running.
There’s no free tier for this service.
Example price:
$1.25 x 24hours x 30days = $900
200 gigabytes of data processed x 0.018 = $3.60
Total: $900 + $3.60 = $903.60
Video on an intro to the SWP:
Check out everything over on the Secure Web Proxy page: https://cloud.google.com/secure-web-proxy